With Microsoft and LinkedIn close on shipping giant’s heels.
Originally posted by The Register by Jessica Lyons Hardcastle
DHL is the most spoofed brand when it comes to phishing emails, according to Check Point.
Crooks most frequently used the brand name in their attempts to steal personal and payment information from marks between July and September 2022, with the shipping giant accounting for 22 percent of all worldwide phishing attempts intercepted by the cybersecurity outfit.
DHL warned customers that it was the target of a “major global scam and phishing attack” on June 28, and noted it was “working hard to block the fraudulent websites and emails.”
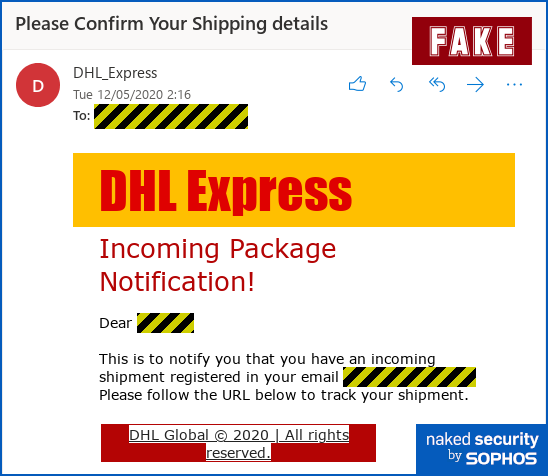
Miscreants used a tried-and-true phony message in the phishing attempts, falsely alerting customers that their package couldn’t be delivered and requesting personal and payment info to proceed with the delivery.
As we saw with the recent Oktapus cybercrime spree, these types of urgent requests — to change a password or, in this case, delivery or payment info — are especially effective at stealing credentials.
Don’t click this
One phishing email observed by Check Point attempting to impersonate DHL was sent from the address “info@lincssourcing[.]com.” Crooks doctored it to look like the sender was “DHL Express,” the security biz noted in the report.
The email’s subject line, “Undelivered DHL(Parcel/Shipment)”, and message also tried to trick the victim into clicking on a malicious link claiming that they need to update their delivering address to receive the package.
Of course, the URL doesn’t really direct a user to DHL’s website. Instead, it leads them to a fake, attacker-controlled website with a form asking the victim to enter their name and password, which are then harvested by the crooks.
These stolen credentials can then be used to nab other account info, such as payment details, or can simply be sold to other identity thieves in dark-web forums.
While DHL tops the list of lifted brands, Check Point says Microsoft is in second place for third-quarter phishing scams, totaling 16 percent of all campaigns cashing in on brand recognition. LinkedIn, which topped the list in both Q1 and Q2 of this year, dropped down to third place with 11 percent.
Victims are more likely to click on a malicious link that looks like it was sent from a trusted brand, which is what keeps the phishing pool stocked. It is an inexpensive crime with a high return on investment for crooks.
Phishing attacks were by far the most commonly reported cybercrimes last year, with 323,972 reported to the FBI and costing victims $44.2 million in losses [PDF].
In another brand-spoofing phish example, Check Point detailed how criminals used a fake OneDrive email to try to steal a user’s Microsoft account information. With this particular scam, the message was sent from “websent@jointak[.]com[.]hk,” used “OneDrive” as a phony sender name, and contained the subject: “A document titled ‘Proposal’ has been shared with you on Onedrive.”
Similar to the DHL spoof, the Microsoft-brand phish attempts to lure the victim into clicking on a malicious link that spoofs a Microsoft web app login page and then enter their account password.
Not that we need to tell you this, but as a general rule, don’t trust emails and especially not those that ask for personal information or credit card details, Check Point warned. Additionally, “think twice before opening email attachments or links, especially emails that claim to be from companies such as DHL, Microsoft or LinkedIn.” ®